Azure Sentinel: New Microsoft SIEM almost free to trial

2019 is the year to invest in learning about Azure Sentinel. A key reason: during the Public Preview period Azure Sentinel services are provided at no extra charge. The economic motivation: popular cloud-based Enterprise SIEM services (Security information and event management) are among the most expensive and business critical cloud services large and high-value organizations contract for. For hybrid cloud customers already vested in Office 365 and Azure Active Directory, the integration of cloud identity management and security analytics with Azure Sentinel can be piloted with
production data at virtually no charge. A finding could be that a pivot to the Microsoft SIEM would increase security, simplify compliance, and dramatically reduce the cost of enterprise security management.
Familiar technologies with new Threat Management tools and workflow
I.T. security professionals in recent years have looked at various Microsoft Azure services and components (like Log Analytics, Azure Security Center, and Azure Monitor) and asked: ‘Does Microsoft have a SIEM, because it seems like all those pieces add up to one?’ The answer has been that Microsoft cloud monitoring products were designed to provide input to customer SIEMs. This made sense because every large enterprise has a SIEM or SIEM-equivalent with often a high investment in a particular SIEM vendor or open source technology.
Not including security data about Azure AD and Office 365 activity would introduce a big blind spot in corporate SIEMs that traditionally have monitored on-premisess directory logins.
Now it seems Microsoft has been working on, and is now ready to share with the public, the “plus” service they have built on top of what was already in Azure. Azure Sentinel provides a framework that is robust and scalable enough so as to appeal to enterprise customers seeking the best value in cloud-based SIEM services. Running on top of familiar and cloud-proven technologies like Azure Logic Apps, Machine Leaning (ML), and the Kusto query language used by Azure Log Analytics, the “plus” pieces are found in the Threat management menus of the Azure Sentinel Overview page: (See figure 1.)
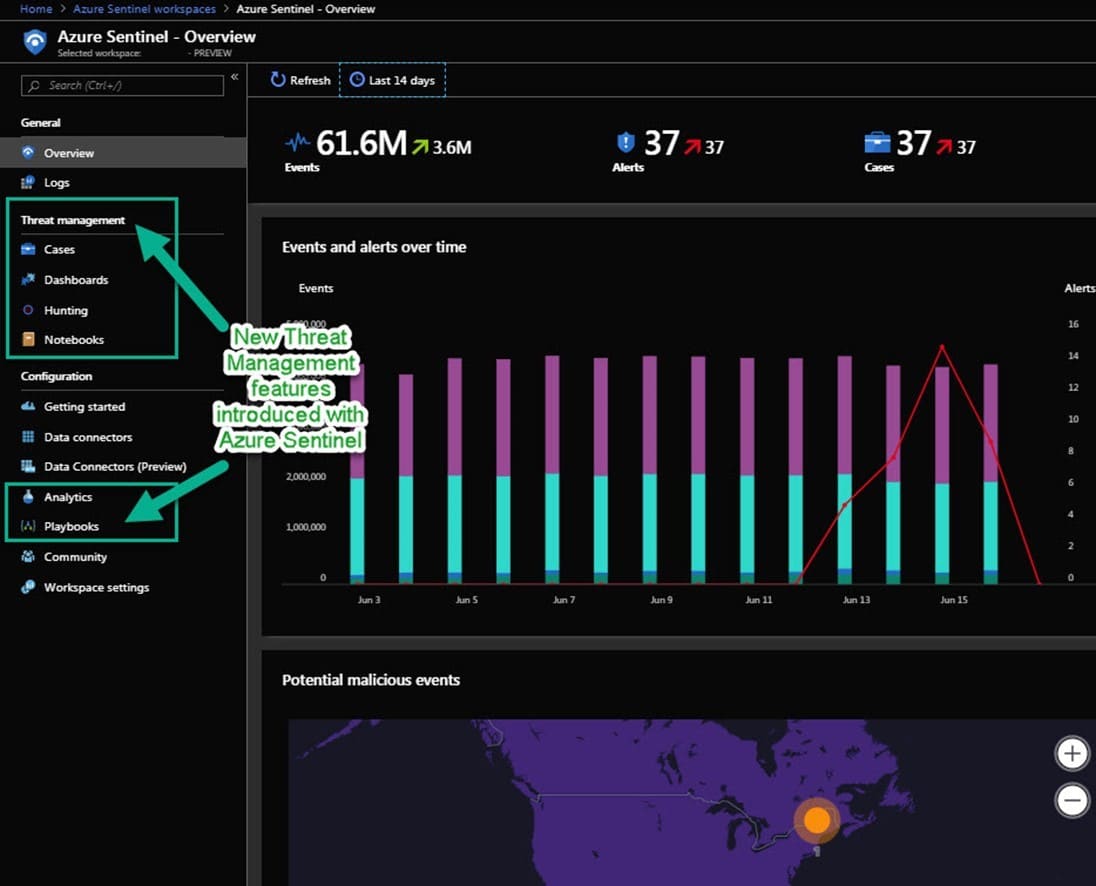
Figure 1 – Overview page of Azure Sentinel (left side)
Be an early adopter of Machine Learning applied to security operations
Microsoft has an amazingly rich amount of Machine Learning (ML) baked into Azure Sentinel. ML is an area of hybrid cloud integration that Microsoft excels in and in this manner cloud security customers can share in the benefit. For example, a ‘Data Source anomalies’ dashboard tile is active out of the box across all your data types (center right in Figure 2). Something that also catches your eye on the lower right of the dashboard is the ‘Democratize ML for your SecOps’ tile:
When you click on ‘Learn More’ on the ‘Democratize ML for your SecOps’ tile, you will open in your browser a Microsoft article: “Reducing security alert fatigue using machine learning in Azure Sentinel”. From that page you can launch the simple Azure Cloud Shell instructions to enable Fusion on your Sentinel workspace: https://docs.microsoft.com/en-us/azure/sentinel/connect-fusion. How it works:
- “Fusion uses graph powered machine learning algorithms to correlate between millions of lower fidelity anomalous activities from different products … to combine them into a manageable number of interesting security cases.”
- Under the covers, “built-in ML uses principles of model compression and elements of transfer learning to make the model developed by Microsoft’s ML engineers ready to use for any organization’s needs.”
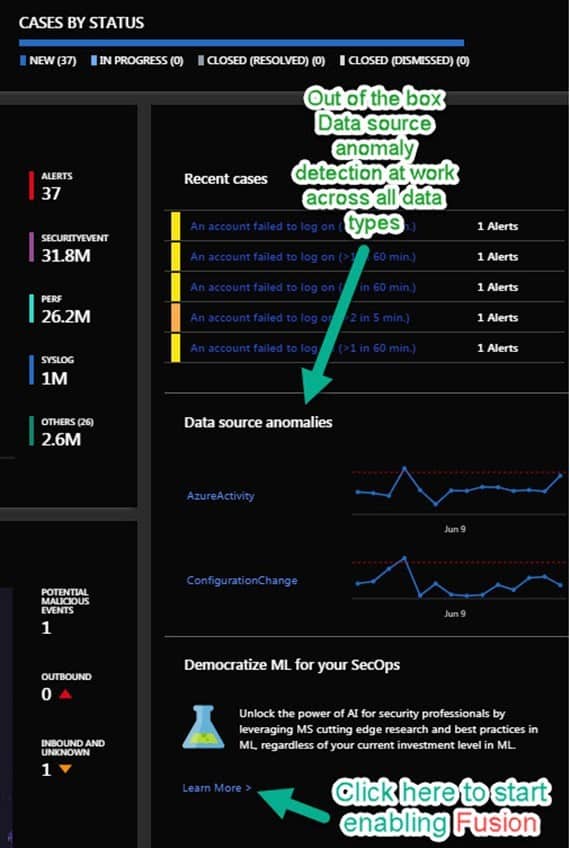
Figure 2 – Overview page of Azure Sentinel (right side): Enable Fusion for more ML features, explore Data source anomalies
Take a look at these high value ML-assisted queries that become available when you enable Fusion with (in this case) Identity Protection and Microsoft Cloud App Security products:
- Anomalous login leading to O365 mailbox exfiltration
- Anomalous login leading to suspicious cloud app administrative activity
- Anomalous login leading to mass file deletion
- Anomalous login leading to mass file download
- Anomalous login leading to O365 impersonation
- Anomalous login leading to mass file sharing
- Anomalous login leading to ransomware in cloud app
Possible IT disasters like those listed above are what keeps security engineers up at night! Azure Sentinel is a legitimate mitigation against these career-ending (and even business-ending) IT security nightmares.
High-level Walk-Through: How Azure Sentinel achieves SIEM workflow
1. Connect data providers to Azure Sentinel (Data connectors menus):
- Common identity and access providers like Azure Active Directory and Office 365, syslog, DNS, Security Events, and Azure Activity
- Additional (premium or optional) Microsoft security components like Azure ATP, Azure Security Center, Azure Information Protection
- Other cloud providers like AWS CloudTrail
- Enterprise security vendors: Palo Alto Networks, Cisco ASA, Check Point, Fortinet, F5, Symantec ICDX, and Barracuda
Many of these data providers will already exist in your Azure or on-premisess estates. It’s just a matter of also connecting them to Azure Sentinel. Examples: Connect Azure Security Center (ASC) = ASC keeps working as before and now events are included in Azure Sentinel. Another example: Connect Log Analytics workspace = all workspace solutions work as before, plus the workspace is co-purposed for Azure Sentinel. Until the Azure Sentinel preview period is over, there are little or no additional charges to connect existing data sources to Sentinel.
2. Use the Hunting feature of Azure Sentinel Threat management to identify queries that produce results of interest, like “Summary of failed user logins by reason”. (See Figure 3.) The pre-populated queries get you starting on creating your own valuable Kusto-based queries customized for your environment.
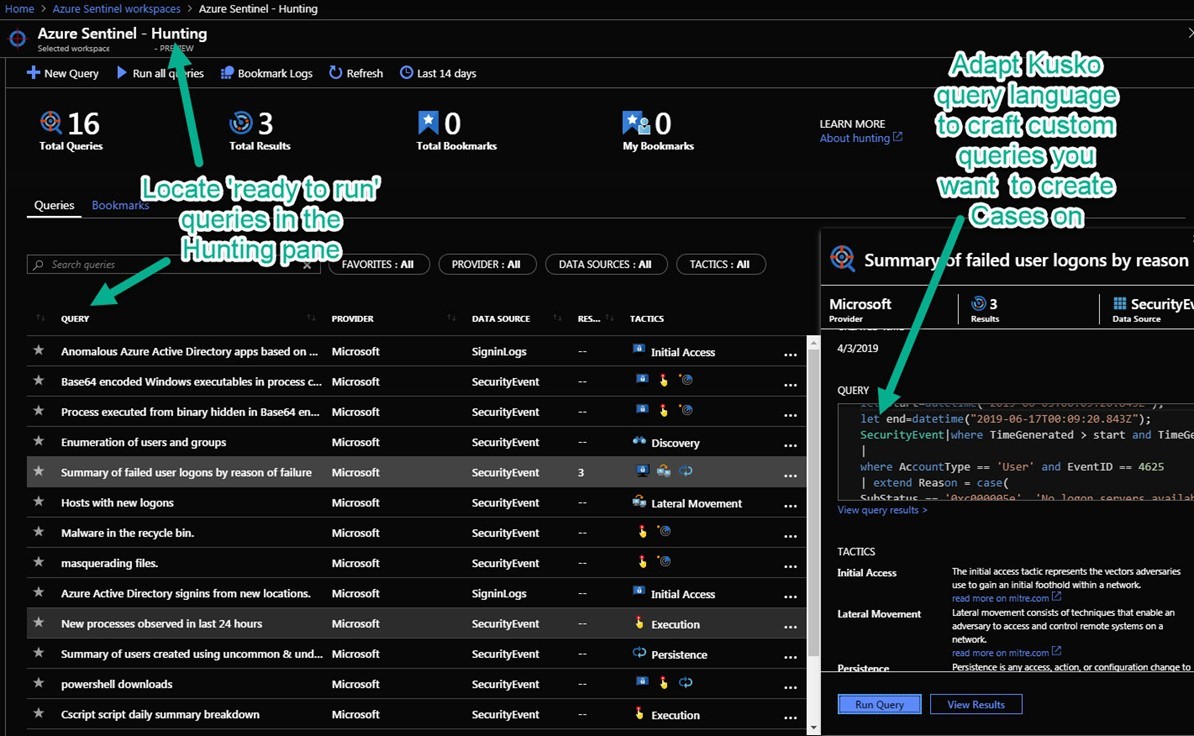
Figure 3 – The Hunting feature helps you craft very specific queries that only return data when you want a case created
3. Use the Analytics section of Azure Sentinel to create alert rules that trigger on the queries you define. For example, a custom query was crafted from the default ‘Summary of failed user logons by reason query’. For this alert rule, we want a Sentinel case to be created every time there are two (2) or more failed logins within any five (5)-minute period. By default an Azure Sentinel case is created for each Azure Sentinel alert.
Tip: Be sure to configure the Entity mapping portion of the alert rule (seen in Figure 4), this helps Sentinel recognize the key data elements in the event when performing investigations.
4. When an Azure Sentinel alert fires, an Azure Sentinel Case will be created. If you have properly configured your entity mapping, Azure Sentinel cases will include a quick summary of the attacked host(s), attacking account(s) and attacker IP address(es) on the Entities tab. Quick-sort columns in the alert list include number of entities and quantity of hits, these help you prioritize cases to investigate. (See figure 5.)
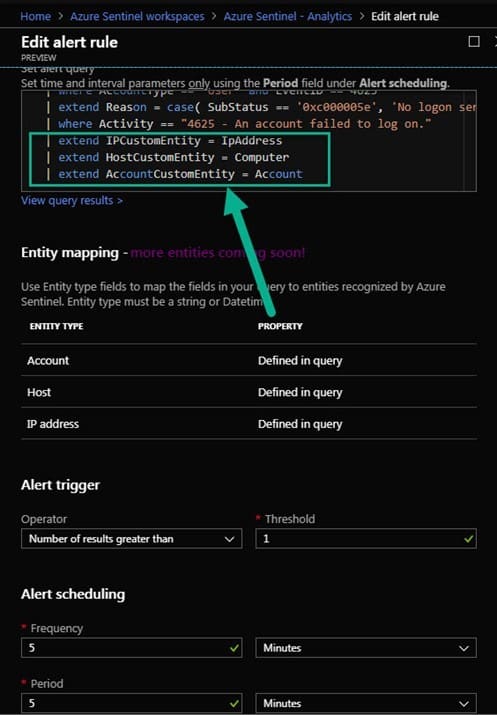
Figure 4 – Define Entity mapping along with the alert query when creating an alert rule
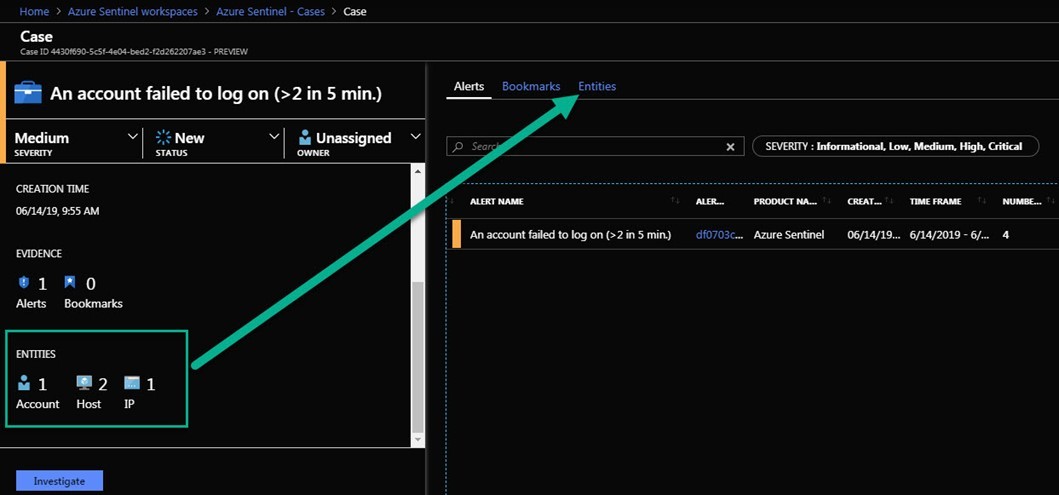
Figure 5 – Azure Sentinel cases include Entities that facilitate investigation
Summary: Start piloting Azure Sentinel now
Microsoft does not recommend using Azure Sentinel in Preview status for production workloads, but it’s very functional already. Introduced in first quarter 2019, there is no official end announced to the preview period, although late 2019 is not unreasonable. So the exact final feature set and license cost for Azure Sentinel remain unknowns. However, as mentioned there is little to no charge to use Sentinel in the preview period and many Sentinel features (which are based on proven Azure micro-services) offer high-value return right now. For a large organization with an existing SIEM, a 2020 availability of the production release is not an unreasonable timeline to begin a pilot of the prospective new SIEM (Azure Sentinel) now. For a smaller organization investigating its first SIEM, a pilot with Azure Sentinel today is a smart, low-cost first step that will produce immediate gains in security posture. Strategically, everyone running their business on Office365 and Azure Active Directory needs to evaluate Azure Sentinel with due diligence as a complement to their security tools roadmap.
Selected resources to learn more
5-Minute Quickstarts and Step-by-Step Tutorials
https://docs.microsoft.com/en-us/azure/sentinel/
Azure Sentinel Pricing
https://azure.microsoft.com/en-us/pricing/details/azure-sentinel/
Quickstart: Get started with Azure Sentinel Preview
https://docs.microsoft.com/en-us/azure/sentinel/quickstart-get-visibility
Machine Learning powered detections with Kusto query language in Azure Sentinel
https://azure.microsoft.com/en-us/blog/ml-powered-detections-with-kusto-query-language-in-azure-sentinel/


Content Provided by:
AIT’s Microsoft MVP
John Joyner, Senior Director of Technology
Delivering next-generation technology management services to customers around the world. John Joyner is a cloud architect that helps businesses stay competitive. Awarded twelve times (2007-2020) as a Microsoft Most Valuable Professional (MVP) in Cloud and Datacenter management. MVPs make up a global community of about 2,000 technical experts and across 90 countries who share a passion for technology, a willingness to help others, and a commitment to community.
Principal industry certifications:
Microsoft Certified Azure Solutions Architect Expert
MCSE: Cloud Platform and Infrastructure — Certified 2018
Microsoft Certified Solutions Expert (MCSE): Private Cloud
CMSP: Certified Managed Services Professional




