The threat of cybersecurity breaches grows in parallel with our increasing reliance on digital platforms. In today’s cybersecurity landscape, a robust cybersecurity framework isn’t a luxury but a necessity. Keep reading for an introductory overview of some of the most commonly adopted cybersecurity frameworks that organizations use to bolster their defenses.
Numerous cybersecurity frameworks exist to help organizations manage risk and reduce vulnerability. Some sources mention up to 25! This post focuses on the four frameworks that are most relevant to our customers:
- NIST Cybersecurity Framework
- ISO 27001
- CIS Controls
- CMMC
Before we start, it’s worth noting that a cybersecurity framework typically consists of guidelines, best practices, and standards that organizations can adopt to mitigate risks and lessen vulnerabilities. They generally have three main components: the Core, Implementation Tiers, and Profiles. The Core offers a set of desired cybersecurity activities and outcomes using easily understandable language. Implementation Tiers assess the extent of an organization’s cybersecurity risk management practices. Profiles align cybersecurity activities with business needs, risk tolerances, and resources.
 NIST Cybersecurity Framework
NIST Cybersecurity Framework
NIST is a powerful tool for organizations to protect and defend their systems from cyber threats, which have been steadily increasing in frequency and severity. It provides a detailed set of best practices that inform businesses of the risks they face and ways to reduce them.
By taking advantage of the framework’s five core functions – Identify, Protect, Detect, Respond, and Recover – businesses can evaluate their cybersecurity strategies, identify vulnerabilities and take necessary action to mitigate possible attacks.
With companies regularly under attack by well-funded and organized hackers, it’s essential to use all available resources to stay one step ahead of the criminals. Utilizing NIST’s detailed advice and recommended processes provides an invaluable shield against attacks and a guide to preparing your business for any crisis.
 International Organization for Standardization (ISO) 27001
International Organization for Standardization (ISO) 27001
ISO 27001, established by the International Organization for Standardization, is a comprehensive and effective security standard suitable for organizations of all sizes. It provides an information security management system by establishing requirements, policies, and procedures to help organizations protect confidential data from unauthorized access.
Companies and organizations comply with these international standards to ensure their information remains secure in today’s world. However, compliance with ISO 27001 does not guarantee absolute protection against a data breach – it aims to minimize risk and ensure that the environment is properly managed and monitored continuously.
Companies can ensure their security efforts align with established industry standards and practices by implementing ISO 27001 procedures like personnel training and risk assessment techniques and developing security policies and frameworks.
 Center for Internet Security (CIS) Controls
Center for Internet Security (CIS) Controls
The Center for Internet Security (CIS) Controls are a set of best practice security measures organizations can implement to reduce cyber security risks. CIS has identified twenty controls, divided into three categories, that can be used as an effective defense-in-depth technique for protecting an organization’s information resources.
For example, the first control is inventory and control of hardware assets, which provides visibility and protection against threats by ensuring all IT systems are up-to-date, secure, and patched with the latest updates. Another control focuses on implementing access restriction policies so employees only have access to systems or data necessary for their job, further helping to protect an organization from malicious actors.
Used correctly, CIS Controls provide organizations of all sizes with a cost-effective strategy for significantly increasing their security posture.
 Cybersecurity Maturity Model Certification (CMMC)
Cybersecurity Maturity Model Certification (CMMC)
Cybersecurity Maturity Model Certification (CMMC) is essential for companies doing business with the US Department of Defense (DOD). It protects controlled unclassified information (CUI) from cybersecurity threats like hacker attacks or accidental disclosure.
To comply with CMMC requirements, companies must demonstrate operational maturity across various cybersecurity controls and practices, from basic hygiene maintenance to advanced threat protection measures. In addition, the CMMC focuses on the entire DOD supply chain to decrease the risk of cyberattacks and ensure that government contractors operate within secure IT infrastructure environments.
Compliance with the CMMC certification strengthens companies’ data protection strategies. It enhances their security posture while giving them access to business opportunities offered by DoD contracts.
Comparing Cybersecurity Frameworks
With the variety of cybersecurity frameworks available, selecting the best fit can be challenging. The NIST CSF is a risk-based framework that emphasizes proactive steps for security improvement. ISO 27001 offers a standards-based approach with audit and compliance requirements. The Center for Internet Security (CIS) Controls provides a comprehensive strategy for data protection. The newest, CMMC, focuses on cybersecurity in the military-industrial supply chain. Each framework has unique strengths and weaknesses, and the choice should depend on an organization’s specific needs, industry, scale, and scope of operations.
Summing it Up
By now, most leaders know cybersecurity is a critical concern for any business, regardless of size or industry. By selecting a framework that aligns with their specific needs, organizations can significantly bolster their defenses against cyber threats.
Specializing in the Microsoft Security Stack, AccountabilIT offers a complete suite of IT services to help safeguard your business against cyber-attacks. Our cloud-first, compliant strategies for workloads and security provide exceptional value for medium and large enterprises seeking to grow. We offer end-to-end IT solutions while ensuring the safety of your data. Business owners must treat cybersecurity as a top priority and ensure that only expert hands implement the necessary protection measures. For a solution custom-tailored to your unique business requirements, consider AccountabilIT.
Contact us today to discuss how we can help!
 Learn More About Cybersecurity Frameworks
Learn More About Cybersecurity Frameworks
From Here to Compliance: Building Your Cybersecurity Roadmap
In this webinar, industry experts John Joyner and Lauro Chavez share valuable insights about the critical components of a robust cybersecurity framework and discuss the most popular cybersecurity frameworks in use today.
You can also listen to this webinar on episodes 1-3 of AIT: The AccountabilIT Podcast.
 International Organization for Standardization (ISO) 27001
International Organization for Standardization (ISO) 27001 Center for Internet Security (CIS) Controls
Center for Internet Security (CIS) Controls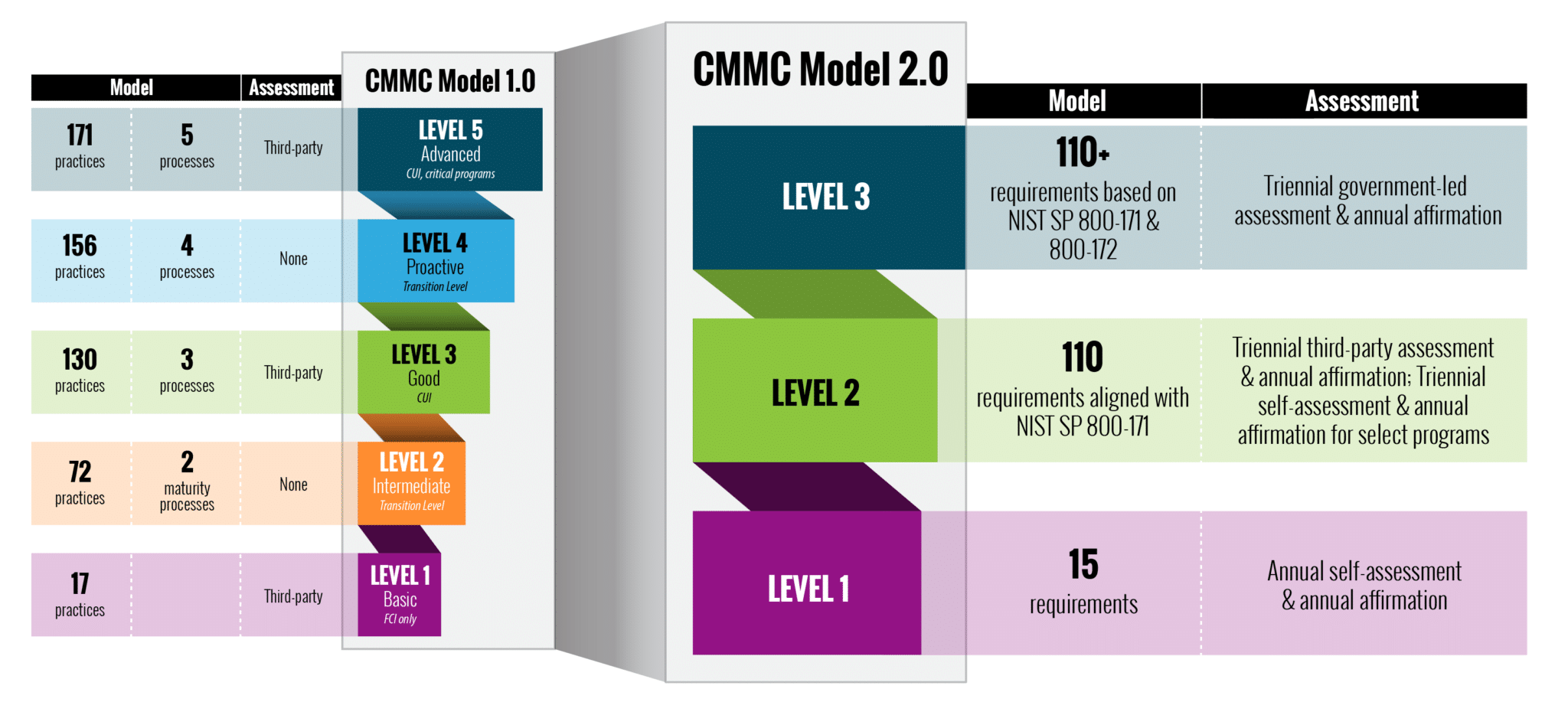 Cybersecurity Maturity Model Certification (CMMC)
Cybersecurity Maturity Model Certification (CMMC)