
New Data Connector UX, AWS live & CyberArk coming.
With little fanfare earlier this month, Microsoft released a significant UX (user experience) update to the Data Connectors component of Azure Sentinel, their new flagship cloud-based SIEM: Connect Data Sources to Azure Sentinel. Read more about the Sentinel Preview in my previous article. The new connector selection and configuration features are a big improvement and make the Sentinel connector experience more scalable and intuitive. Also this month an AWS CloudTrail connector went live and a new CyberArk connector appeared in a Coming Soon status.
New Data Connectors experience.
Properly connecting your sources of security audit data (such as Active Directory (AD) or Azure AD logins, and firewalls) to your central security analysis tool is obviously a critical step in accurate setup of your SIEM.
Figure 1 shows off the new Azure Sentinel Data Connectors blade, here some management features to note:
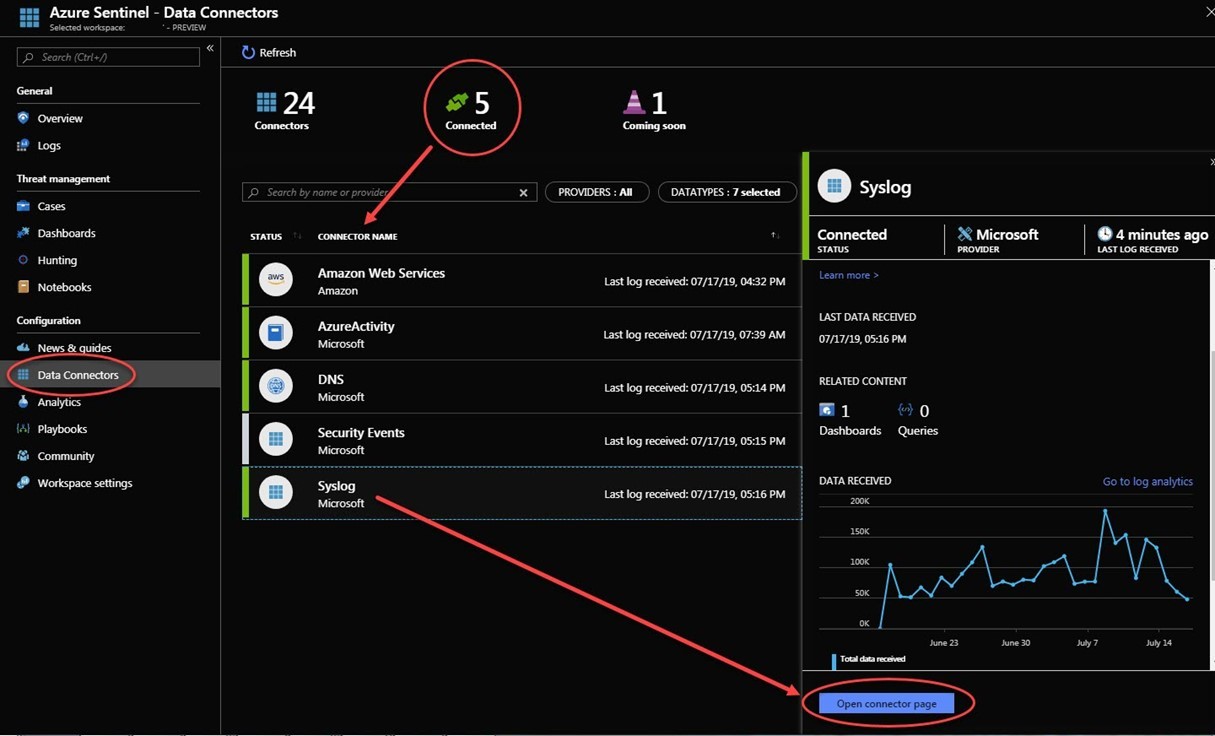
Figure 1 – Azure Sentinel Preview Data Connectors blade
You want to make your SIEM setup as simple and transparent as possible to reduce human error and maximize security effectiveness. The new Azure Sentinel connector UX makes it easier to detect malfunctioning connectors and to learn when new connectors are available. Rolling all the selection and configuration settings of a wide variety of internal and external security data sources into one place, using a consistent UX is a big plus when evaluating an enterprise SIEM.
Figures 2 and 3 walk you through identifying, learning about, and proceeding to integrate a security audit source with Sentinel, in this example Azure ATP:
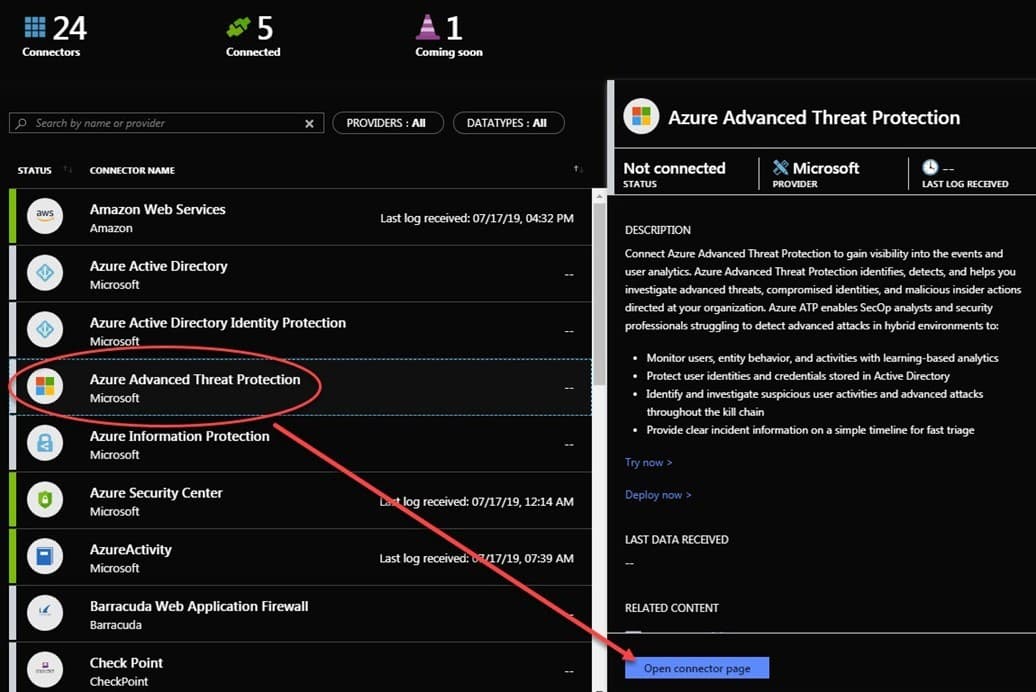
Figure 2 – Browsing available Azure Sentinel connectors
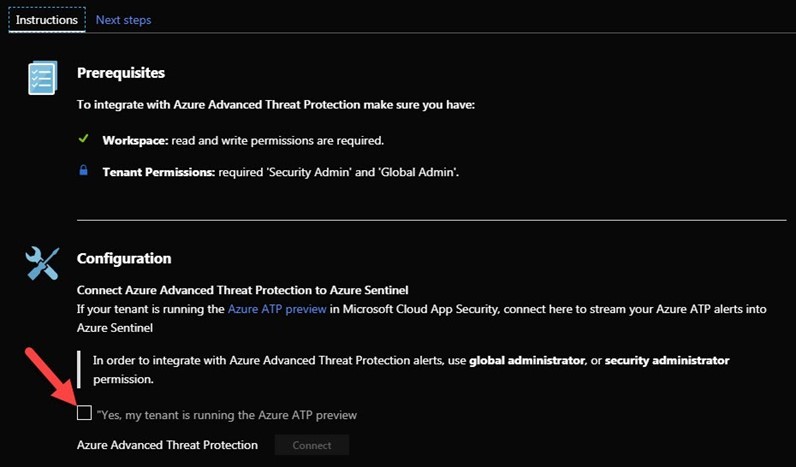
Figure 3 – After clicking Open connector page, the Instructions and Next steps for that connector are displayed
Amazon Web Services connector is released.
Amazon Web Service (AWS) is the market leader in public cloud share and many organizations have both Azure and AWS estates. In fact, dividing critical enterprise I.T. components across both Azure and AWS, to achieve a cross-public cloud fault tolerance is a nirvana solution on many architects’ roadmaps. For customers investigating using Azure Sentinel and who have AWS resources in scope for security management, deploying the AWS connector is the right decision.
Azure Sentinel connects to AWS via the Cloudtrail service (aws.amazon.com/cloudtrail/). AWS Cloudtrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services. After adding the AWS Connector to your Sentinel workspace you’ll find two new dashboards, AWS User Activity and AWS Network Activity. Figure 4 shows live data from the connector’s User Activity dashboard.
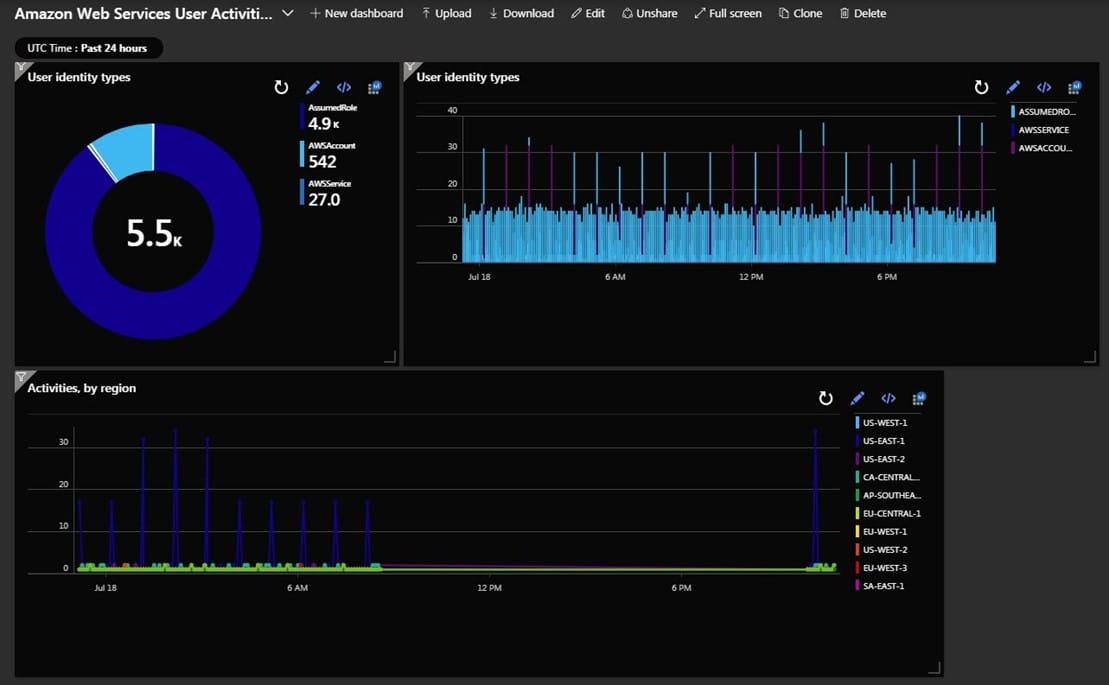
Figure 4 – The AWS Connector to Azure Sentinel has useful dashboards out-of-the-box
When setting up the Azure Sentinel connection to AWS CloudTrail, you will need to know the Role ARN of the custom Azure Sentinel role you created in your AWS IAM. Follow these steps to expose the Role ARN: “Connect Azure Sentinel to AWS CloudTrail” https://docs.microsoft.com/en-us/azure/sentinel/connect-aws. After pushing the Open Connector page button on the AWS connector, a blade will appear pre-configured with your Azure account and Sentinel workspace ID, all you need to do is paste the ARN string as shown in Figure 5 then press the Add button.
There are some valuable AWS security dashboard widgets out of the box, they include:
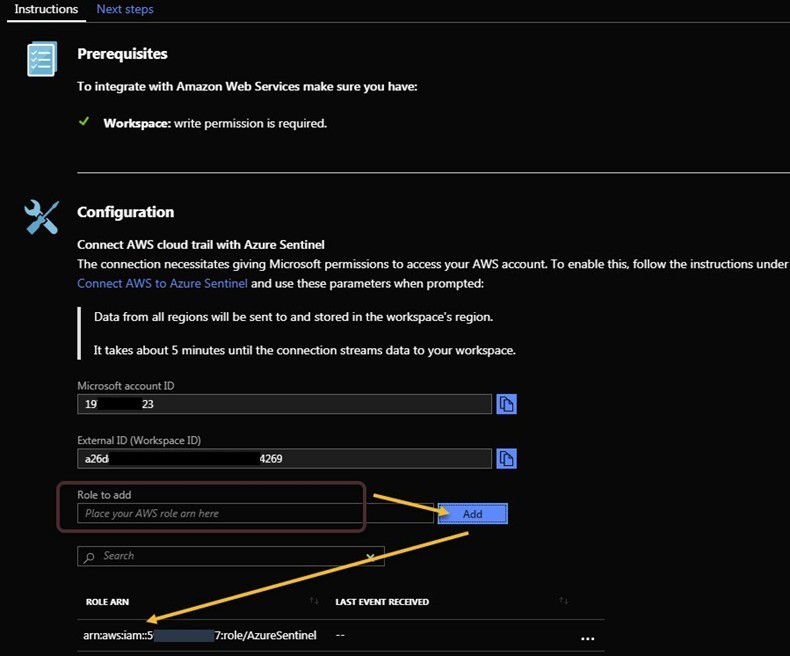
Figure 5 – Quick and easy configuration of the AWS Connector, after you do the necessary work in AWS IAM
New CyberArk connector coming.
A new syslog-based data connector for CyberArk customers was just announced and is already shown in the Sentinel Preview in Coming Soon status (Figure 6).
What is CyberArk?
They are an information security company offering Privileged Account Security. The company’s technology is utilized primarily in the financial services, energy, retail, healthcare and government markets. From their website (www.cyberark.com): “[Sentinel] integration gives users the ability to aggregate CyberArk privileged threat data with data from complementary applications and systems.
Users are able to tap into Sentinel’s built-in AI for analytics to create dashboards, have a central and comprehensive view across Azure instances and connect disparate data to identify and act upon security risks quickly.”
Figure 6 – New CyberArk connector to Azure Sentinel coming soon
A review of useful Sentinel queries out of the box for the CyberArk connector include:


Content Provided by:
AIT’s Microsoft MVP
John Joyner, Senior Director of Technology
Delivering next-generation technology management services to customers around the world. John Joyner is a cloud architect that helps businesses stay competitive. Awarded twelve times (2007-2020) as a Microsoft Most Valuable Professional (MVP) in Cloud and Datacenter management. MVPs make up a global community of about 2,000 technical experts and across 90 countries who share a passion for technology, a willingness to help others, and a commitment to community.
Principal industry certifications:
Microsoft Certified Azure Solutions Architect Expert
MCSE: Cloud Platform and Infrastructure — Certified 2018
Microsoft Certified Solutions Expert (MCSE): Private Cloud
CMSP: Certified Managed Services Professional



